Freelancer Identity Theft: It Happened to Me—Here's What You Should Know
Freelancer identity theft happens all the time. In fact, someone’s likely had their identity stolen as you read these words. Let’s hope it wasn’t you.
In this post, Toptal Software Engineer Relja Damnjanovic shares his story about freelancer identity theft and offers lessons for freelancers, who don’t want to learn things the hard way.
Freelancer identity theft happens all the time. In fact, someone’s likely had their identity stolen as you read these words. Let’s hope it wasn’t you.
In this post, Toptal Software Engineer Relja Damnjanovic shares his story about freelancer identity theft and offers lessons for freelancers, who don’t want to learn things the hard way.
Relja has extensive corporate and freelance experience, and a computer science engineering degree. He’s a certified Magento expert.
Expertise
Several weeks ago, I was thinking about hiring myself for a project I had in mind. Sounds crazy, right? That’s because it is, and I wouldn’t be doing it had I not been a victim of identity theft!
I’m sharing my experience with fellow freelancers because there is nothing crazy or funny about what I learned along the way. I learned my lesson the hard way, so you don’t have to. That’s why I’m writing this article and why you should read it.
It all began with a Skype chat.
I was contacted by someone on Skype, claiming he hired me through a freelancing network and after some time working on a project, he figured out that that person was not as skilled as he claimed to be, leading the client to discover that the freelancer, in fact, was not me!
The client shared every detail, contact, and profile with me, and as I reviewed the information, I was shocked.
This impostor was intensely posing as me. His profile was filled with all of my personal information: My profile picture, stolen from Facebook, the portfolio and skills section, lifted from my Toptal profile, along with content taken from sites, namely LinkedIn.

How does this happen?
After further digging, I realized that this doesn’t just happen to a few random people here and there. It’s quite commonplace, and it’s become a significant problem!
As in many other industries, this is considered stealing intellectual property in order to gain a competitive advantage, and it is particularly evident in the world of freelancing.
Unethical people create profiles on open freelance networks, pretending to be someone with much more experience and expertise than themselves. They use the stolen profile to poach jobs, and set higher prices than they’re worth.
Open freelance networks do not run thorough background checks on applicants, which means they have little control over the content their members put up online.
In failing to vet their members, they create a platform that can be abused by identity thieves.
Bear in mind that I am not saying they are enabling fraud on purpose. It comes with the territory. We’re talking about open networks, which have lax background checks by design. Otherwise they wouldn’t be open, would they?
On the other hand, clients looking for hiring freelancers often take what is written in their portfolio at face value. They conduct interviews without visual contact, or simply place too much trust in people on the basis of online communication.
This makes them easy targets for unethical people to take advantage of. They use fake profiles to land real jobs, and make real money.
How do you know if you’re a victim?
For the most part, this is pretty straightforward.
Simply Google your name, and search for yourself on the biggest freelance platforms.
However, keep in mind that some platforms allow their users to remain invisible to the public, meaning you might have to create a profile on the platform, and log in before you can search.
Again, this might not be enough, especially for people with common first or last names, since a search could yield many results.
Identity thieves also use alternate spellings and make other changes to keep their fake identity under wraps.
How do I prevent this from happening?
You can’t. At least not with 100 percent efficiency.
So, what can you do?
Well, you can and should take steps to protect your privacy.
No solution is bulletproof, but it doesn’t have to be. Your solution just needs to make every step of identity theft tricky and time consuming, in order to deter the attacker. In short, by improving your security, you’re forcing attackers to look for softer targets.
Here are a few simple solutions.
-
Consider cross-pollinating links to your profiles on all public networks you use, email and email signature, Skype account, and so on. If you have your own website, link your Toptal profile there too, your Skype account, LinkedIn, Facebook, Twitter, and any other network you use.
-
On each of these sites, clearly state that these are the only accounts you are using. If someone does a background check and realizes they’re communicating with a different account, it should raise an alarm and compel potential clients to request additional information (hopefully, from one of your real accounts).
-
To further protect yourself, take some time to create accounts on various freelance networks, even if you don’t plan on using them. Making a duplicate profile on a network that already has your legitimate profile is difficult, and fraud is easier to detect. In the end, if a fake profile actually appears on a network, you’ll have your original profile with which to file a complaint.

Please keep in mind that neither of these measures guarantees you won’t fall victim to identity theft.
Think of it this way: If you install a cutting edge alarm system in your car, that doesn’t guarantee it won’t get stolen. But it does mean that a car thief is more likely choose a soft, unsecured target instead, thus reducing their exposure to risk and increasing their chances of success.
The same principle of deterrence applies to online security. You don’t have to create a bulletproof way of protecting your professional identity; you merely need to take precautions that will make it harder to steal and therefore not worth the trouble.
It’s time for an industry crackdown.
Why do I find a seemingly minor issue so important? After all, we are talking about small-time freelancers and the financial damage is not that great. Compared to the overall cost of identity theft and intellectual property theft, it’s negligible.
For starters, it’s not about money.
We’re all professionals.
All freelancers work hard for their reputation. Having someone pretending to be you can put all this at risk, and potentially cause serious and long-lasting damage to your professional reputation. Just ask Susan Greene, a copywriter who had her identity stolen on Elance.
Clients, who hire identity thieves, are victims of fraud, too, and once they realize that, they are likely to turn to you, because they don’t know who else to turn to.
You don’t want a stranger contacting you out of blue to ask about money sent to you for a job you never finished. But, sometimes it happens, and sometimes, the client will turn to you for help.
Professional networks targeted by such fraudsters (like Toptal) face reputational and financial risks, so they’re victims too.
The immediate financial impact of identity theft on freelancing platforms might not seem that great, but the reputational risks are, and in the long run, they can cost you dearly. That’s why the industry needs to take this issue seriously, and take additional steps to prevent identity theft on their platforms.
We’re all in the same boat, and it’s about time we start acting like it.
Why my lessons may apply to you.
Well, the answer is obvious - because it happened to me!
At first, I laughed.
But after two weeks of back-and-forth emails with the freelance network support team, I got really frustrated. I kept receiving generic responses, claiming the platform was working on my case and thanking me for bringing this to its attention.
At one point I asked to send them an ID scan so they could actually verify that I was who I claimed I was.
So, they verified my account, but it still didn’t help. I still received messages from support, stating that it couldn’t inform me about the outcome of the investigation because it needed to protect the member’s privacy.
This was downright wrong on many levels since I was the person whose privacy was violated.
In the end, I had to dig deeper myself.
I found something called a Digital Millennium Copyright Act (DMCA) Takedown Notice.
The DMCA notice is essentially a complaint any person can file if their copyrighted material is being used without their consent.
Note: DMCA abuse is becoming commonplace, and some poorly informed people try to use DMCA notices to remove legitimate information they find troubling or offensive. This is an extremely unethical and risky practice, as people filing baseless DMCA notices can be prosecuted in most jurisdictions. Do not play around with DMCA notices! Use them only when you are certain you’re filing a legitimate claim against an offender who violated your copyright. Whenever in doubt, seek advice from a qualified professional.
How do you file a DMCA takedown notice?
There are some services that will navigate the entire process on your behalf, but these services aren’t free.
If you’re not comfortable handing off your DMCA claim to a third-party, you can do it yourself, but you need to be patient and do some due diligence.
Step one: Locate the correct person to send the notice to. To do this, find out who the legal representative is at the company that owns the site with the infringing material, and also check where the site is hosted.
Next, see if the company/ISP has an online form for submitting DMCA takedown requests, and use those if possible.
If not, then you can file it in the email form. Companies have legal@ email addresses for this sort of communication and you can use Headreach or Email Hunter if you need help. If you are asked to file it in a different format, or send it to a different email, comply with the request promptly since it’s the fastest way of getting it resolved.
You will have your homework before you shoot off a DMCA notice:
- Take plenty of time to prepare your DMCA notice letter.
- Be pleasant: Do not argue. It will not get you anywhere.
- The notice should be signed by you, and it should contain details about the copyrighted material, such as who wrote it.
- Set aside time to prepare an additional document that details everything stolen from you.
- Include links and screenshots, such as links to your original work.
The more comprehensive you are, the faster the entire situation goes away.
Remember to include all of your contact information, and an additional statement explaining the problem and attesting to the legitimacy of your notice
You can see a sample DMCA Takedown Notice here.
The asterisk indicates information you should complete yourself. It’s very similar to the one I sent, and the outcome was effective; the fake profile was removed in less than three hours.
For more information about DMCA takedown procedures and a legal perspective, check out Sarah Hawkins’s website. Her article helped me get out of my predicament and saved me a lot of time.
Should you take legal action?
This is a tricky question.
Open freelance networks usually protect themselves through their Terms of Service (TOS), meaning that they are not responsible for the content uploaded by their users. Therefore they cannot be held liable, just like you can’t sue Facebook when someone creates a fake profile in your name.
However, you can take on the individual, who used your material and stole your identity. This leads us to an obvious predicament: Because the thief is pretending to be you, you don’t know his or her real identity.
While open freelancing platforms can help, it doesn’t mean they will help. In my case, the network probably knew who the impostor was – at the very least through his or her IP address and payment gateway account. But it wouldn’t share the information with me because “they need to protect their user’s privacy,” per their TOS.
This means the burden of proof falls solely on you.
I did consider a less conventional option.
I wanted to create a fake profile for myself, and offer a job to the identity thief, in hopes of learning more about their actual identity. I decided against it because that would make me unethical as well.
What if I hire contractors?
In these incidents, there are multiple victims who should share part of the responsibility. They include:
- The freelancer whose identity has been stolen.
- The client who hired the unqualified freelancer.
- The freelance network the attacker misled and abused to get the gig.
The legitimate freelancer is exposed to multiple risks.
The identity theft may cause severe reputational consequences, which could eventually lead to financial losses, plus, a freelancer can get entangled in the dispute between the client and impostor.
Freelancers who fall victim to identity theft must waste resources, addressing the issue, trying to get the offender banned while clearing their own name.
Clients who hire an impostor don’t get what they pay for: They end up paying senior rates to a clueless thief.
Clients affected by fraud won’t just lose money. Just like freelancers protecting their identity, clients will be compelled to take action, which will cost them resources, as well. Such incidents can dramatically hurt their business, depending on what the impostor was working on.
Due to the volume of work and number of members, open freelancer networks simply don’t have the resources to vet every single applicant.
These networks aren’t liable and won’t suffer immediate financial consequences, but the risk to their reputation is very real. It is in their best interest to weed out bad apples and maintain a good name.
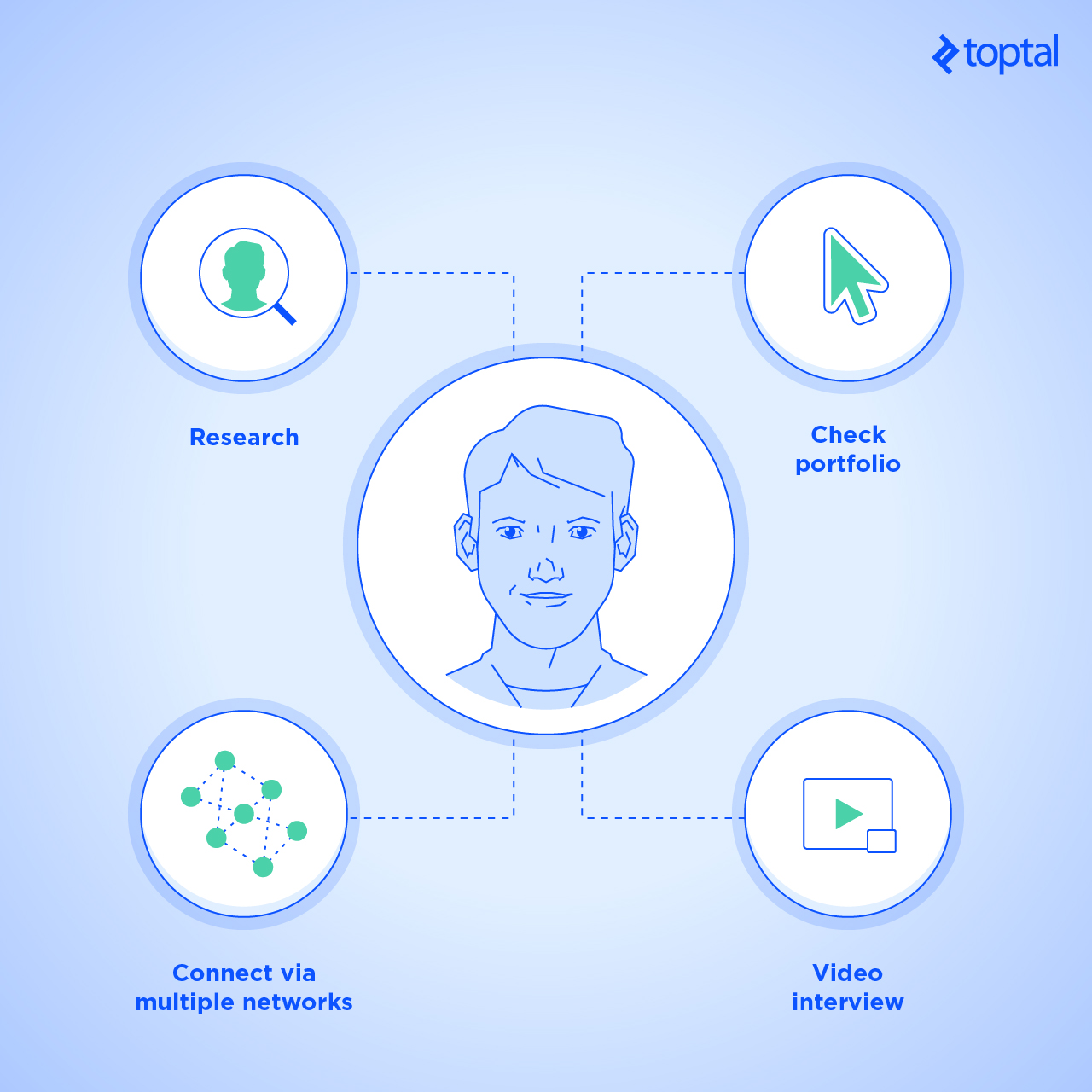
Here’s how clients can protect themselves from impostors:
- Do the following every time you hire someone:
* Research the candidate. Google them, and look at all their online profiles. See what you can learn about their professional skills and experience. Further, check if any of the profiles you find link to the website/platform you found the candidate on. You can also consider using Headreach and Email Hunter to check the email they are using. * Check the portfolio. Click on all the links provided by the freelancer. Don’t just look, check! See if those are live and functional websites. A broken link may suggest that the site went down at one point in the past, but also that it never existed. Therefore, if there’s not a link to a live website, then chances are it’s just made up. Or perhaps the developer cannot provide a link to some of her work due to NDA restrictions. Nevertheless, you can always ask her about it, without requiring the candidate to reveal anything that’s covered in the NDA. * Schedule a video interview. If you schedule an interview, make sure it’s in the form of a video chat. Today, it’s considered common courtesy to use your webcam when speaking with someone online for the first time. It’s a way of getting to know each other, which is always important, because it builds trust. It’s just like you would get to know the candidate in person if they were applying for a non-remote job - Try the following, if you can: * Get an expert opinion. If you’re an expert in the field you’re hiring for, you can properly vet the candidate, and gauge their knowledge and previous experience yourself. It’s not easy to screen technical candidates when you’re not an engineer yourself so get someone else to do it for you. * Contact their former employers. Ask for a reference. If you contact four or five of their references, at least one person is likely to respond. Don’t ask too many questions, or request too much information. You should be able to get a general feeling from their responses. * Consider adding additional steps to your hiring process. When vetting “unvetted” freelancers, try to come up with open-ended interview questions designed to expose potential fraudsters. You could also try a more personal approach, and ask questions based on the freelancer’s bio: personal stuff that a fraudster might not have picked up. For example, come up with a question that involves some of their Facebook likes, related to music, TV, clubs, and so on.
- If you believe you have contacted an impostor, here’s what you should do: * Try to connect with them on multiple networks. Ask the candidate to send you to other profiles on publicly available networks, such as LinkedIn. Let them know you want to add them as a contact there. Then message them through LinkedIn instead of your standard communication channel, and wait for a reply, which you can use to gauge whether or not you’re talking to the same person. There’s always a chance the real freelancer will accept your LinkedIn request without even looking, which is why it’s crucial to message them on the platform. Making a duplicate profile on one network is not that difficult, but making multiple profiles on several networks is. Should the attacker choose to create multiple accounts, each one will increase the chance that someone along the way will discover the attempt, and notify the real freelancer. * Use Skype for communication. Once you add the freelancer to your contact list, you can check the “current timezone” box in their profile. Check if that matches the timezone of the city they’re supposed to be in. However, use good judgement. The freelancer could just be on holiday, visiting their family, or just be a digital nomad. Ask them where they are, and see if their explanation makes sense.
Be cautious, not paranoid!
My advice to clients hiring online talent is simple: Pay attention, especially when you recruit from an open network.
If your friend recommends a freelancer, then you can be sure you’re going to be fine, but if you pick someone you found online, please make sure to set aside time for research and background checks. I am aware that this is a tall order, as every hour spent vetting candidates is an hour you could have spent on something more productive.
To make matters worse, many clients turn to online hiring at the worst possible moment – when they realize they won’t be able to meet their targets and need fresh blood on short notice.
Setting aside a few days for communication with potential candidates and background checks is an obvious dilemma if the client is rushing to meet a deadline.
However, the potential risk of hiring a fraudster outweighs the time spent on a reasonable background check.
Why do I say a reasonable check? Because under no circumstances should you create a hiring process that freelancers will find Draconian or too cumbersome. Otherwise, you run the risk of alienating legitimate professionals, who may perceive you as an unreasonable client with ridiculous expectations.
Competent freelancers tend to get plenty of jobs, so they might not bother with clients who doubt them right off the bat. That’s why it’s crucial that clients do most of the heavy lifting themselves.
Don’t ask freelancers to provide loads of background information, references, and samples. Ask for as little as possible, but take a surgical approach, and focus on key issues and concerns that can be addressed with as little effort as possible.
What’s the use of receiving good replies, if you’re asking the wrong questions?
Can this happen on Toptal?
Toptal is not an open freelance network. You can’t just signup, and create a profile on your own.
Toptal employs a complex application process through which all candidates are screened and vetted.
Contracts are signed with both parties – clients and developers – and people are assigned to an overview role of the project, which makes the environment extremely unsuitable for identity thieves.
Let me put it in more colorful language. Trying to trick Toptal with a fake identity is a bit like trying to invade Russia in November, wearing nothing but flip-flops and Speedos.
While this sounds reassuring, it also exposes Toptalers to risk: If someone is looking for a qualified freelancer to impersonate, they needn’t look further than Toptal’s ever-growing pool of talent to find a target.
Be responsible, and protect yourself.
Online identity theft happens all the time. In fact, someone’s likely had their identity stolen as you read this article. Let’s hope it wasn’t you.
Identity theft can cause a range of serious problems to multiple parties. It may end up costing you a lot of time, stress, and money. This applies to freelancers, clients, and freelance networks, including Toptal, albeit indirectly.
Freelancers must dedicate some time to protecting their online identity and intellectual property. Clients should be aware of these risks. Open freelance networks should offer additional support in cases of suspected identity theft.
Ultimately, everyone has to do their part for the greater good of the industry. It’s in everyone’s best interest.
Just like your home, your reputation is yours alone, and you alone should reap the benefits of it. Keep it safe, and don’t let malicious impostors near it.
Further Reading on the Toptal Blog:
- Cybersecurity Spotlight: Preparing Your Organization for Deepfake Voice Clone Fraud
- Exploring the Bear Case of the Cryptocurrency Bubble
- Why Internal Corporate Software Is So Frustrating (with Infographic)
- Business Is Booming: A Guide to E-commerce UI/UX Design for Older Consumers
- Exploring the Post-crash Cryptocurrency Market: Blockchain, Regulations, and Beyond
Belgrade, Serbia
Member since October 17, 2012
About the author
Relja has extensive corporate and freelance experience, and a computer science engineering degree. He’s a certified Magento expert.

