Understanding the Cybersecurity Landscape in 2021
More than a year after the onset of COVID-19, organizations must shift from temporary stopgap measures to more robust cybersecurity strategies and technologies. Here’s how to keep your company safe.
More than a year after the onset of COVID-19, organizations must shift from temporary stopgap measures to more robust cybersecurity strategies and technologies. Here’s how to keep your company safe.

Melissa Lin
Melissa has worked at tech startups, as well as in management consulting, advising Fortune 500 companies across multiple sectors.
Expertise
You may have heard the saying, “Never let a crisis go to waste.” Unfortunately, hackers have taken that notion to heart during COVID-19. The number of cyberattacks soared as hackers repeatedly exploited vulnerable back doors into corporate systems amid the distraction caused by the pandemic. Targets included healthcare, financial services, and public sector institutions like the World Health Organization. Attacks against the financial sector increased 238% globally between February and April 2020.
According to Alissa Abdullah, Deputy Chief Security Officer at Mastercard and former Deputy CIO at the White House under President Barack Obama, COVID-19 and the resulting shift to virtual work “has changed the adversary’s opportunities, and shifted their focus on some of the other tools that we’re using.”
Hackers also attacked collaboration platforms. In April 2020, hackers got ahold of more than 500,000 Zoom account usernames and passwords, and sold them in dark-web crime forums for as little as a penny per account; some information was simply given away. Cyberattacks involving the COVID-19 vaccine also emerged; in December 2020, the European Medicines Agency reported that some data on the Pfizer/BioNTech COVID-19 vaccine was stolen during a cyberattack. Around the same time, IBM sounded the alarm over hackers targeting companies central to COVID-19 vaccine distribution.
Expect More Cyberattacks to Happen More Swiftly
Cyberattacks and their associated costs are only going to continue accelerating. Consider the following: Cybersecurity Ventures predicts that cyberattacks will occur every 11 seconds in 2021, nearly twice the 2019 rate (every 19 seconds) and four times the 2016 rate (every 40 seconds). It’s estimated that cybercrime now costs the world $6 trillion annually, double 2015’s total of $3 trillion. By 2025, cybercrime is projected to cost the world $10.5 trillion each year.
The price tag of cybercrimes includes the theft of intellectual property and personal and financial data, as well as actual money—plus the cost of post-attack disruptions to business, lost productivity, and reputational harm, among other things, explains Steve Morgan, Founder of Cybersecurity Ventures. In addition to these direct consequences, cybercrime’s hidden costs also include increased insurance premiums, lower credit ratings, and legal fees due to customers initiating litigation.
A 2020 IBM Security report that surveyed 524 breached organizations in 17 countries across 17 industries indicated that the average cost of a data breach was a whopping $3.86 million and took an average of 280 days to contain. The consequences may continue for years following the incident.
Under Attack: Spear Phishing, Social Engineering, and Vishing
In the UK in 2019, 90% of data breaches were due to human error. During the pandemic, employees have been preoccupied with amplified personal and financial stress, rendering them more vulnerable to spear phishing—a type of phishing that targets specific people or groups in an organization—and “social engineering” attacks designed to psychologically manipulate individuals into revealing sensitive information.
More specifically, social engineering attacks aim to deceive employees into doing something that seems legitimate but is not. Although companies typically train employees to identify fraudulent requests, amid the pandemic’s abnormal circumstances it has become harder for employees to differentiate scams from legitimate requests.
“Everyone knows you can’t pick up a USB in a parking lot [and put it into your computer], but training sophisticated employees on fake emails from bosses is still a real problem,” says Thomas Ruland, a finance expert in the Toptal network and Head of Finance and Operations at Decentriq, a company that specializes in secure data sharing and collaboration. “When you’re not in the same office, accidental data sharing may happen more often. When people are working in the same physical office, you can just ask, ‘Hey did you really send this?’ but it’s harder to parse through when working from home.”
The issue of “vishing”—voice phishing—has also been exacerbated by the pandemic, with attackers using calls to obtain VPN credentials or other sensitive information from employees. Vishing scams often attempt to seem legitimate by providing prospective victims with an accurate piece of personal information, such as an individual’s Social Security number or bank account number. A surprising amount of other personal information is publicly available for attackers, who need only scour social media platforms or other associated websites to access such details.
Exploiting Weak Spots in Cloud Security
COVID-19 spurred the hasty adoption of new technologies as organizations instituted new digital processes amid the disruption to in-office work. In the earlier stages of the pandemic, many companies had no choice but to accept new risks, including reduced control standards, to maintain operations.
One of the major outcomes of such rapid and dramatic changes was widespread cloud adoption. In its 2021 State of the Cloud Report, Flexera found that remote work demands pushed more than half of the surveyed group to increase their cloud usage beyond what had been planned. Other respondents indicated that their organizations might accelerate migration given difficulties in accessing traditional data centers and delays in their supply chains. While 20% percent of enterprises revealed their annual cloud spend exceeded $12 million, an increase of 7% from the previous year, 74% reported that their costs exceeded $1.2 million, up from 50% the previous year.
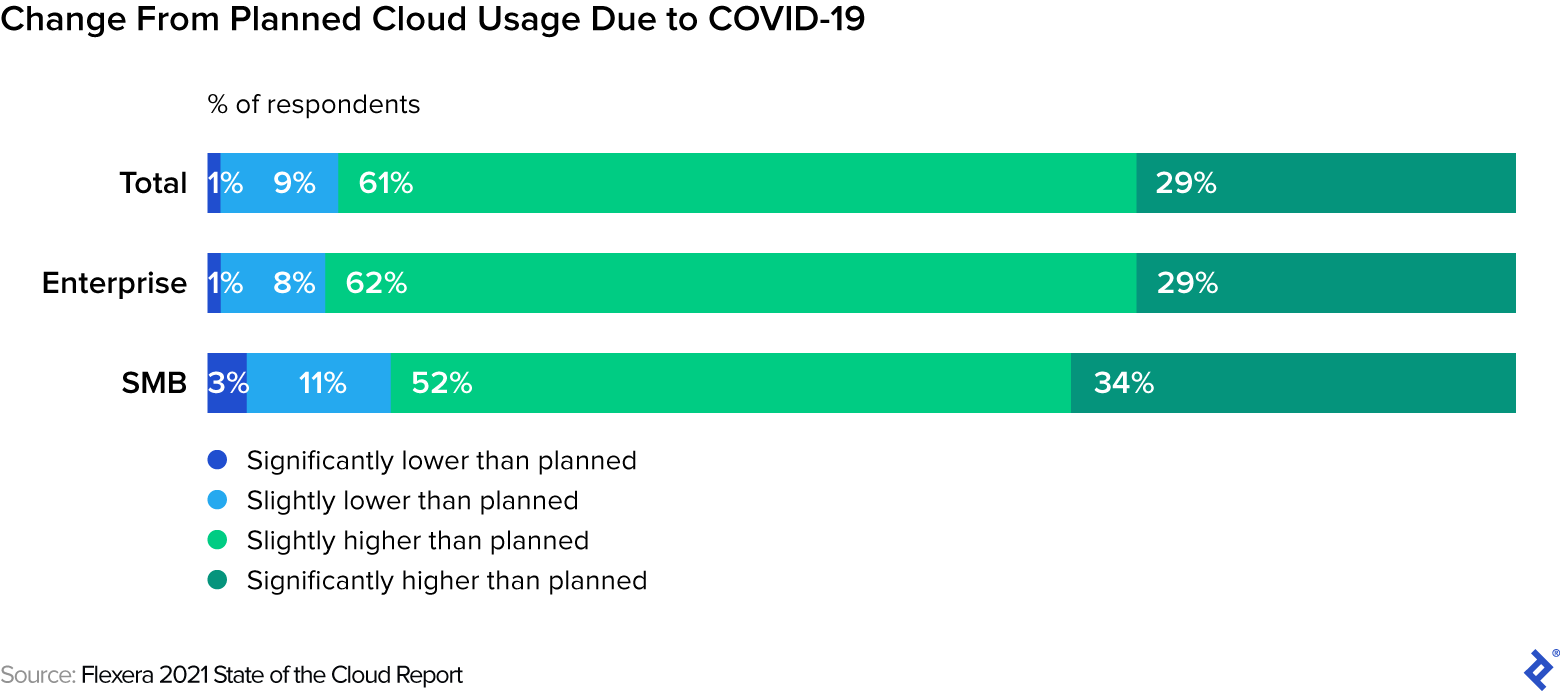
Unfortunately, actions taken under extreme time and operational pressures have inevitably led to gaps in cybersecurity. And 75% of respondents in Cybersecurity Insiders’ 2020 Cloud Security Report indicated that they were either “very concerned” or “extremely concerned” about public cloud security. Cloud security concerns are further exacerbated when organizations use two or more public cloud providers, as 68% of respondents do.
Security experts and employers are primarily concerned about three cloud security challenges. First, cloud and container misconfiguration, when an administrator inadvertently deploys settings for a cloud system that conflict with the organization’s security policies. Another is limited network visibility, in which an organization is unsure of what hardware and software are connected to the network and what network events are transpiring. And the third major concern are unprotected cloud runtime environments, which provide opportunities for attackers to prey upon an organization.
Employee Usage of Unauthorized Personal Devices and Networks
COVID-19 and the shift to virtual work prompted widespread adoption of bring-your-own-devices programs. Especially in the early stages of the pandemic, many workers had no choice but to use personal devices, public Wi-Fi, or home networks to work remotely. Such circumstances provide an opening for hackers to access organizational resources; when personal devices are compromised, they can serve as launchpads into the corporate network.
“One of the biggest cybersecurity risks is the personal device,” Trina Glass, an attorney with Stark & Stark told the Society for Human Resource Management. “Whether smartphone or laptop, there are serious problems posed by using personal technology in a work setting involving sensitive information. Employees might save documents to their desktops or send document drafts to their personal email. They may not have up-to-date antivirus software, or they may use outdated personal password protection.”
Supply Chain Attacks and Third-party Risks
In December 2020, news broke that SolarWinds, a major IT management firm, suffered from a cyberattack that went undetected for months. Earlier that year, foreign hackers had broken into SolarWinds’ systems and inserted malicious code. Subsequently, when SolarWinds sent out software updates to its 33,000 customers, the attackers’ code went with it and created a back door to customers’ IT systems. The hackers used these back doors to install additional spy malware. Ultimately, around 18,000 of SolarWinds’ customers installed these updates, including US agencies such as the Departments of Homeland Security and the Treasury, and private companies such as Intel, Microsoft, and Cisco.
Hackers often target and attack insecure elements of the software or hardware supply chain. Accenture found that 40% of cybersecurity attacks originate from the extended supply chain. Attackers typically seek the weakest links such as small vendors with few cybersecurity controls or open-source components. More often than not, after identifying their target, hackers add back doors to legitimate and certified software or compromise systems used by third-party providers. Thus, supply chain attacks expose the truth that an organization’s cybersecurity controls are only as strong as the chain’s weakest link.
What Can You Do to Improve Your Company’s Cybersecurity?
Now that the world is more than a year into the pandemic, companies must move beyond simply instituting stopgap measures and instead anticipate the “next normal.” Chief information security officers, CFOs, and cybersecurity teams must figure out how their workforces, customers, supply chains, and sector peers will work together to provide adequate cybersecurity. Here are five ways to start:
Enhance Vigilance Around Access: Zero Trust and Multifactor Authentication
Traditional IT network security is based on the castle-and-moat concept: Everyone inside the network is trusted by default, and it is difficult for those outside the network to obtain access. Cyberattacks that took place during the COVID-19 pandemic have exposed this strategy’s limitations. Companies should consider adopting a zero-trust strategy that maintains stringent access controls and does not trust any individual, device, or application by default—even those already inside the network perimeter. A zero-trust model requires identity verification and authorization for every person and device attempting to access resources on a private network. In 2019, Gartner predicted that by 2023, 60% of enterprises would move from VPNs to zero-trust initiatives.
Further, enterprises should mandate two-factor authentication for employees. Two-factor authentication requires a user to provide two different types of information to access an online account or IT system; typically, this includes a username/password pair (single-factor authentication) and another proof of identity, such as a code sent to an employee’s phone or email address.
The World Economic Forum recommends that businesses also begin the transition toward biometric multifactor authentication using fingerprints, faces, typing behavior, or other factors to verify users’ identity. In contrast to companies that store their customers’ passwords on their servers, user biometrics are stored on the user device, and thus, there is no single data collection point for cyber criminals to access and the risk of online fraud and identity theft is greatly reduced. The global biometric system market size is projected to grow from $36.6 billion in 2020 to $68.6 billion by 2025.
Rethink Supply Chain and Third-party Risk
To bolster cybersecurity, organizations must examine their security tools and requirements for sharing and maintaining private information with vendors. Organizations should begin by reviewing all vendors and potential shadow third-party services; assign risk tiers to vendors, delineating those most critical to operations and having the greatest access to vital information; and then calibrate assessment scope correspondingly.
Enterprises should then update controls and access restrictions for third parties, and develop more robust data-loss controls. Organizations must also ensure that vendors that aren’t currently prepared for heightened cyber risk commit to developing cyber preparedness plans to safely handle information and interact with organizations’ corporate networks. Further, where possible, enterprises should integrate critical third-party logs into enterprise security monitoring and create alert systems for coordinated monitoring and response. Taking all these steps will help build cyber resilience across supply chains.
Develop and Enhance a Cloud Security Skill Set
As organizations move away from traditional on-premises cybersecurity solutions and toward cloud-centric architectures, they must learn to defend the cloud.
Cloud and container misconfiguration can be an issue because, in contrast to an on-premises network where only IT professionals can set up and deploy network infrastructure, in a cloud environment, far more people can do so. Attackers often leverage misconfigurations to access a network because they are easy to spot. Organizations can help manage misconfigurations by following Gartner’s Market Guide for Cloud Workload Protection Platforms to establish a baseline for assets connected to the network. (The full report is available for purchase here.) From there, organizations should monitor those assets for deviations and potentially employ automated defense measures to protect their systems against attacks.
As for network visibility, asset discovery tools provide device discovery and an awareness of not only what is in the network but also which assets are unprotected. These tools provide transparency into the relationships between assets, their usage, the network, and other devices, including which software modules are installed on the network.
Lastly, organizations can defend against unprotected cloud runtime environments for containerized workloads. When a device attempts to run an application, runtime environments act as a middleman between the application and the operating system.
Use Artificial Intelligence and Machine Learning
Although human security analysts already employ automation tools to extract the most urgent alerts from massive datasets and trigger humans to take action, artificial intelligence (AI) and machine learning (ML) tools are becoming increasingly sophisticated.
“We’re moving beyond algorithms that just look at your metrics and tell a human to do something about a certain outlier,” Splunk’s Vice President of Engineering and Head of Machine Learning, Ram Sriharsha, says in the company’s 2021 Data Security Report. “As a matter of scale, we need algorithms and automation that take action. In the security domain, we won’t just train models on past bad actors and behavior to identify new, similar behavior. We’ll see algorithms that just look at what’s happening—look at traffic, look at data—to identify bad patterns and take evasive action.”
Organizations should consider the use of self-learning, AI-based cybersecurity management systems. However, as AI/ML cybersecurity solutions develop, so do attackers. Using adversarial learning, bad actors glean enough about an AI/ML model to design ways of poisoning the system and rendering it ineffective for defense. Adversarial learning is akin to, say, tricking an autonomous vehicle into misunderstanding a stop sign. And according to Gartner research, 30% of all AI cyberattacks will leverage training-data poisoning, AI model theft, or adversarial samples to attack AI-powered systems through 2022. Yet despite these threats to AI/ML systems, a recent Microsoft survey revealed that 25 out of 28 businesses indicated they did not have the right tools in place to secure their AI/ML systems. Don’t be one of them.
Launch Interactive Employee Cybersecurity Training
Though seemingly simple, it is critical for organizations to enhance employee training around cybersecurity measures. Organizations should design role-based training programs and exercises to increase awareness around new cyber risks in a remote environment, including new threats, rules for approved device usage, and processes to report cyber incidents.
Management teams should also provide simulations and walk-throughs for cyberattack scenarios to actively engage employees. Management should also provide clear guidelines around required actions and when decisions should be escalated.
Lastly, employees should be reminded not to use public Wi-Fi networks or printers and not to store documents on home computers.
Staying Vigilant Against Cybersecurity Risks
To respond to escalating cyberattacks in the form of social engineering and supply chain attacks, and increasing shadow IT and vulnerable stopgap measures, enterprises should focus on adjusting to the “next normal.” That is, management must partner with cybersecurity teams to increase vigilance around access, rethink supply chain and third-party risks, develop cloud security skill sets, leverage AI and ML tools, and enhance interactive employee training. Creating secure environments for customers gives businesses a competitive advantage and builds trust and loyalty with their current and future customers.
Understanding the basics
What is the projected cost of cyber crime in 2021?
It’s estimated that cybercrime now costs the world $6 trillion annually, double the $3 trillion in 2015. By 2025, cybercrime is projected to cost the world $10.5 trillion.
What is cybersecurity and how does it work?
Cybersecurity refers to the collective methods, technologies, and processes to help protect the confidentiality and integrity of computer systems, networks, and data against cyberattacks or unauthorized access. Tactics include comprehensive risk assessments, multifactor authentication, AI solutions, and more.
What are the biggest cyber threats?
Some of the largest cyber threats include spear phishing/social engineering attacks, cyberattacks designed to psychologically manipulate individuals into revealing sensitive information; database exposure, when sensitive data is left exposed for anyone to see; and attacks on cloud security infrastructure.
